Enhancing Android Security: A Comprehensive Hardening Guide
Written on
Why Strengthen Your Android Device Security?
In this guide, we will explore effective strategies to enhance the security of your Android device by implementing industry-standard best practices such as CIS benchmarks, recognized cryptographic protocols, and privacy-focused applications. This is essential reading for anyone with an Android device, so let’s dive into the crucial steps for bolstering your security.
1. The Importance of Hardening Android Devices
At the beginning of 2022, Proofpoint researchers observed a staggering 500% increase in mobile malware attacks in Europe. It's evident that cybercriminals are recognizing the growing value of mobile devices, particularly in a remote work environment. Alarmingly, over 80% of Android devices are reported to be vulnerable to at least one out of twenty-five identified security weaknesses. The implications of these vulnerabilities could be severe for both personal and organizational sensitive information.
It is, therefore, crucial to adopt all necessary measures to secure and configure your Android devices properly, preventing them from becoming another statistic. This guide aims to provide you with all the fundamental security references and best practices required to keep your device safe.
2. Security Benchmarks and Standards
2.1. CIS Benchmark
The Center for Internet Security (CIS) produces comprehensive documents, including CIS benchmarks, that are widely utilized by both individuals and businesses. CIS benchmarks are globally recognized documents that outline prescriptive baseline security protocols for hardening various systems, including Android operating systems. Key recommendations from the CIS Android OS benchmark include:
- Keeping your device updated.
- Implementing a secure screen lock.
- Avoiding connections to untrusted networks.
However, always assess your specific context when applying security controls, considering potential trade-offs. For instance, at Deep Dive Security, we prioritize privacy and chose not to follow recommendation 1.19 (L1) which would have allowed Google to collect usage data. Users must fully understand the implications of each recommendation and consult relevant documentation for informed decision-making.
2.2. U.S. DoD STIG
Similar to the CIS benchmarks, the U.S. Department of Defense (DoD) provides Security Technical Implementation Guides (STIGs). These guides serve a similar purpose as CIS benchmarks but are tailored for a U.S. DoD baseline. When deciding which standard to adopt, regulatory requirements may dictate your choice, but in many cases, it will depend on what best suits your needs.
For example, while the CIS benchmark recommends enabling a screen lock without specifying password complexity, the U.S. DoD STIG mandates a minimum password length of six numeric characters. This distinction could be significant based on your threat model.
3. Securing Communications
Beyond baseline security configurations, we believe that Android hardening should encompass core user functionalities, particularly communication security.
3.1. Messaging
Messaging is one of the primary functions of any Android device, yet many messaging applications depend on insecure SMS/MMS protocols that transmit messages in plain text over open networks. Enter the Signal Protocol, a cutting-edge messaging protocol that provides end-to-end (E2E) encryption, adopted by major corporations like Google and Microsoft.
Due to its advanced security features, the Signal Protocol has become the de facto standard for messaging security. Users can enhance their messaging security by utilizing the Signal app available in the Play Store.
3.2. Emails
With over 333 billion emails sent daily worldwide (Statista, 2022), securing email communications is as vital as messaging security. Users should ensure their email practices adhere to E2E encryption models. While this guide focuses on end-user email clients on Android, various technical measures exist to prevent email spoofing and phishing, such as SPF, DKIM, and DMARC.
Most reputable email clients manage encryption automatically. For instance, Proton Mail guarantees E2E encryption for emails sent between Proton users and offers additional options for non-Proton recipients. Users can explore the Proton Mail app in the Play Store for enhanced email security.
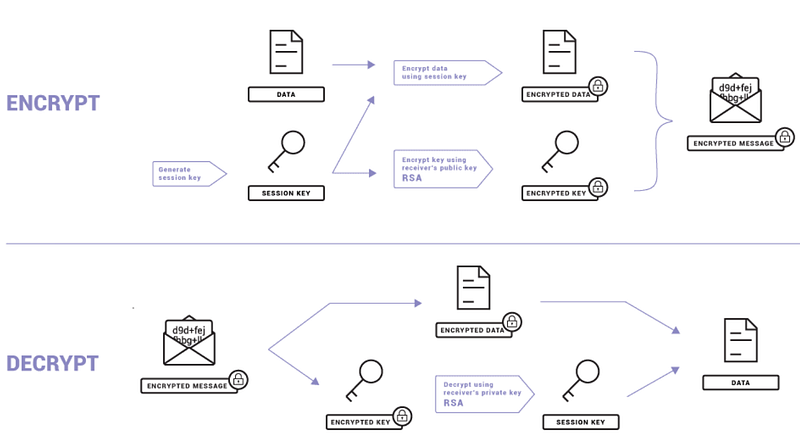
4. Utilizing a VPN for Enhanced Security
If you're reading this, you've likely encountered virtual private networks (VPNs) before. While many use them for accessing geo-blocked content, VPNs also offer significant security advantages, particularly for public Wi-Fi users or individuals in heavily censored regions.
A VPN creates an encrypted tunnel between your device and the internet, ensuring that your Internet Service Provider (ISP) and other potential snoopers cannot view your data. However, users should perform due diligence when selecting a VPN provider to ensure it meets their security needs.
For those seeking privacy-centric options, I recommend NordVPN, which is based in Panama, operates under a no-logging policy, and offers payment options in cash or cryptocurrency.

5. Additional Apps and Security Measures
Having addressed baseline security measures, messaging, email, and VPNs, we now turn to a defense-in-depth strategy in case your device is compromised. For Samsung users, the Samsung Secure Folder offers a robust solution. This feature utilizes Samsung Knox technology to separate, encrypt, and protect data.
Users can store sensitive files and apps in a secure environment, ensuring that even if the main lock screen is bypassed, there remains an additional layer of security to protect critical information.
While Samsung Secure Folder is one option, several other apps on the Play Store provide similar functionality. Always verify the security claims and documentation for any app you choose to use.
6. Quick Security Checklist
To ensure you've covered all security bases, follow this checklist:
- Review and implement the Android CIS benchmark.
- Review and implement the U.S. DoD Android STIG.
- Download and use a messaging app that supports the Signal Protocol.
- Set up PGP or S/MIME for email encryption.
- Ensure SMTP, POP3, and IMAP connections are secured with TLS.
- Evaluate, select, and configure a reputable VPN.
- Employ additional security measures like app lockers and secure file storage.
Chapter 2: Essential Security Videos
This video covers critical security measures every Android user should know to enhance their device's protection.
This video serves as a guide for modern security researchers, focusing on mastering Android security research techniques.
References
Ready to elevate your cybersecurity knowledge? Follow for the latest industry best practices and insights.